This session covers the various Investigations and Terms Related to Computer Forensics.
Presentation Files:

Empowering Your Business with Cutting-Edge Technology Solutions
Congratulations! You made it! You achieved it. Now make sure you secure it.
If you just passed an exam and had an urge to post a picture with your certificate or if you just retired or were just hired by your dream company, you posted a picture of your ID card or your certification, then this article is for you. Hundreds of these pictures are now showing up online on websites that are soliciting fake degrees, certifications, jobs, and more.
While you are proud of your accomplishments make sure you do not post your photos publicly which reveals your name, certificate, and other details. A photo with a face and a certificate in your hands can be used to advertise anything and an acquaintance of mine recently shared a disturbing story.
This individual, whom I call Mr. Good. had recently passed his CISSP exam and like most of us, had posted it on LinkedIn. Mr. Good is a very private person normally but LinkedIn is a social community that he spends most of his time socializing. Thanks to tens of different controls on privacy on LinkedIn, it has gotten even more confusing when you post an update. So out of mere excitement and innocence, he posted his picture. He was proud. A few days later, he discovered, by accident, a photo circulating on Facebook with several others soliciting the sale of illegal certificates such as CISSP and other exams.
That was it for Mr. Good, he immediately removed his picture from his post. But wait, his stolen photo from LinkedIn is being used by someone claiming to be him. Mr. Bad did not even bother to blur out Mr. Good’s name on the certification photo. This would take several attempts, which included contacting Facebook to remove this post. While Facebook is looking into his query, which by the way is probably 1 in a million. It will continue to be online until it is removed.
Here are some examples that I found online.
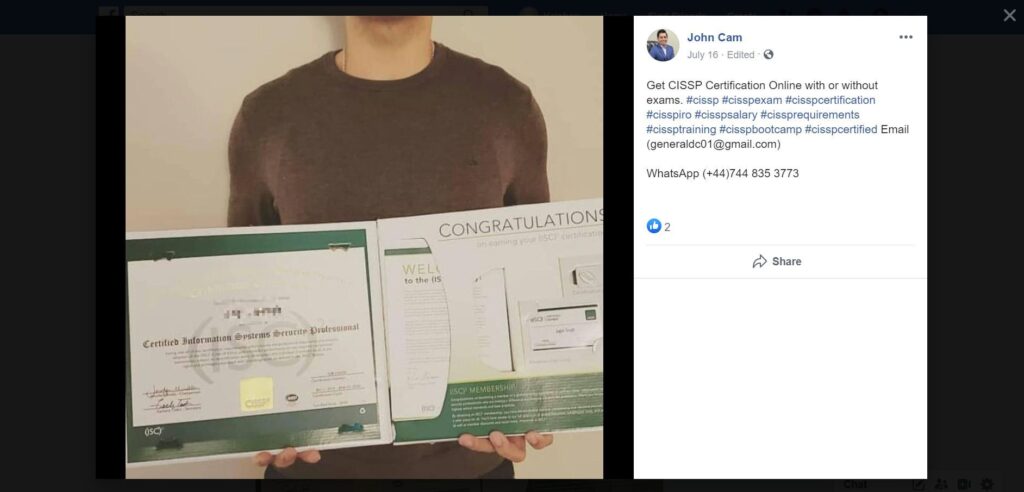
Real Example 1:
John Cam (Fake Name) claims to sell CISSP Certificates on Facebook with the image on the side. He was a little generous and clipped the picture to remove the face. Image1 is taken from a publicly posted image on LinkedIn profile post, Image 2.
I have pixelated the face to protect the individual.

Real Example 2:
Here is the same individual who is selling illegal certifications, this time it is IELTS Certifications without writing the exam. Not sure how it works or if it is a money-making scheme by fraud.
I have already reported this individual on Facebook but upon doing a simple web search, I found this individual/group has posted at several popular web services such as TripAdvisor, Pinterest, Medium.

What can you do?
If you come across such advertisements or postings, simply report as Spam or use the methods provided. For example, TripAdvisor provides an option on a photo to report. Pinterest provides a feature on their pins and users to be reported.
Do not take photos of your employer ID cards, Certificates, and Degrees and post them publicly. I understand we all have a tendency to post on social media such as LinkedIn, Facebook, Instagram but think about the profound negative effects on your identity if these posts and images were exploited.
Over and Out! Stay safe, think before you click (anywhere).

If you would like to subscribe to this blog. Simply follow me on LinkedIn or Twitter and you will see any new alerts and posts directly on these two platforms.
This session covers the various Testing Methods and Types in SDLC Phases with loads of Questions and a Quiz in the end.
Presentation Files:
This session covers the most common types of Threats and Vulnerabilities namely,
Presentation Files:
This is Episode 1 of Security Bits.
On July 17, Billions of people woke up checking their favorite NEWS sources and social applications but about 400 of them fell for a scam on twitter. Famous people like Elon Musk, Jeff Bezos, Bill Gates and companies like The Cash App, Apple and several others including some politicians, they woke up with their personal or private twitter account being used by the attackers who had left a tweet on their behalf. Which basically claimed that these individuals or companies were feeling generous and were going to double your donation through Bitcoin transactions.
I want to speak a little more detail into how the attackers hacked these accounts, then discuss what was the result of such a attack and how significant it is for a company like Apple, Shell, Etc and also how it impacts you, your co-workers, your family and friends.
Prior to the attack on the 17th, the attackers had already infiltrated the Twitters internal systems by using a technique called Social Engineering. So, what is Social Engineering? It is the use of deception to manipulate individuals into divulging confidential or personal information that may be used for fraudulent purposes. The key words here are “use of deception to manipulate individuals”. An example would be calling you and manipulating you to provide your social security number.
So the Twitter employees were trciked into providing their administrative crentials for twitters internal system such as their usernams and passwords.
After which the attackers disabled the protections on the Twitter Accounts such as 2 Factor Authentication, changed the owners email address on file to their own email address and simply reset the passwords and then logged into the accounts. Then sent a tweet and also downloaded their personal Twitter Account Data.
A total of 130 Twitter accounts were affected and this resulted in 400 induviduals sending bitcoins worth a total of $121,000 USD to three seperate Bitcoin accounts in less than 5 hours before Twitter locked down the accounts and deleted the tweets.
So what are the lessons learned from this attack?
I will leave you with couple of thoughts.
Smartphones and Cloud Applications have created tremondous possibiliies but unable to control these can set us back both financially and mentally.
Remember, even if you have not been on twitter or Facebook or LinkedIn or maps, your apps are constantly capturing anything that is useful from within your phones, your GPS Coordinates or your conversations and create a valuable resource for them to sell and if bad guys get hold of it then they can do the same.
You are not the customer, you are the product.

How can I not have an article on Disaster Recovery and Business Continuity Planning? A must have understanding for anyone in Security.
If you are a security professional with years of experience, then you are very familiar with these important fundamental metrics that is used in developing a Business Impact Analysis (BIA) Report which will identity your business processes , identify resources required for recovering of these processes in the event of a disaster and a become part of your Business Continuity Plan (BCP).
The metrics I am referring to are RPO, RTO and WRT. Also, Maximum Tolerable Downtime. I hope someone who is just getting into security and trying to grasp this concept will find this explanation very useful.
Example:
Let us assume a business which is operating normally represented by the following chart. Note, the X axis represents Time. The concepts that we are going to learn are a function of time. Time scale = 1 hr
Normal Operation.
Figure 1
Disaster Strikes.
Figure 2
Recovery Efforts Begin
Figure 3
Normal Operation Resumes
Figure 4
A disaster hits a business which is under normal operation at 3 am, recovery starts at 6 am, normal operation resumes at 8 am. Then we can define the terms as follows:
Maximum Tolerable Downtime (MTD) is defined as The amount of time business process can be disrupted without causing significant harm to the organization’s mission.
For this particular example, from Figure 4 shows a RTO of 3 hrs and WRT of 2 hrs. The MTD is calculated as follows:
MTD = RTO + WRT
MTD = 3 hrs. + 2 hrs.
MTD = 5 hrs.
This is a very simple example for understanding the concept of calculating the Maximum Tolerable Downtime. For a deeper understanding I recommend indulging into books and materials written on DR and BC. Note that there is a very thin line and it can get blurred between resuming total business normal operation which may mean that you have switched back to the primary site for operation. For practical purposes , getting back to normal operation is more critical and important than returning to the primary site.
If you would like to get more understanding of these topics please see the following references:
A technical article on RTO Vs RPO by msp360.com
A blog post from Default Reasoning by Marek Zdrojewski
I have been asked several times, at several occasions about this mysterious term called OT. While it stands for Operational Technology, what is Operational Technology?
Few years ago, I stood in front of a large audience from diverse backgrounds such as Process control, Maintenance, IT and management and delivering a motivating speech on cybersecurity for manufacturing, while I had never used the word OT in the context of Industrial Control System, the word existed but not necessarily used as commonly as today.
While different individuals use it differently to describe their trade, especially in Industrial Cybersecurity practice, the word itself has become somewhat of a open secret, we think we know what it means, but do we really? So to tackle this problem, I asked a bunch of people in my closest professional circle and tried to define it myself. While the definition of OT might change, but as far as I am concerned, what I am about to tell you will still be relevant because instead of defining all the different systems that the Operational Technology represents, I will simply define what it represents.
So here you,
Operational technology (OT) is a set of hardware, software, and communication systems that are used to monitor, control, and automate industrial processes. OT systems are typically used in critical infrastructure industries such as manufacturing, energy, and transportation.
These can include IACS and Control System Components, Information Technology components that are part of the control systems etc., but are defined by the organization to appropriately apply the necessary security measures and controls.
Lets look at a diagram. Yes, that is MS Paint and I did create it 5 years ago. As you can see, OT, Operational Technology is an umbrella term defined by the organization to include systems such as Industrial Automation and Control systems (IACS), Fire Systems, Access Control Systems, Lighting Controls etc.

What is the relevance of defining Operational Technology?
The importance of defining OT for your organization is simply to be able to develop / design and implement appropriate security controls and measures to protect your business operations. Properly identifying what falls inside the OT environment and what falls outside, what is included and what is excluded, will provide you with the right information to develop your OT Cybersecurity Strategy.
Do you have any comments or suggestions to improve this definition? Send me a message.